Subscribe Subscribed Unsubscribe. Powered by ThreatCloud Intelligence. Did you find it helpful?
To provide organizations with the best level of protection, security experts should be attuned to the ever-changing landscape and the latest threats and attack methods. The ThreatCloud cyber attack map from Checkpoint Software shows historical data that is reset each day at 12:a. The map is more visual than the one from Norse, but. The term refers to the deployment of malware, particularly viruses, that clandestinely observe, sabotage or destroy data in the computer systems of government agencies and large enterprises.
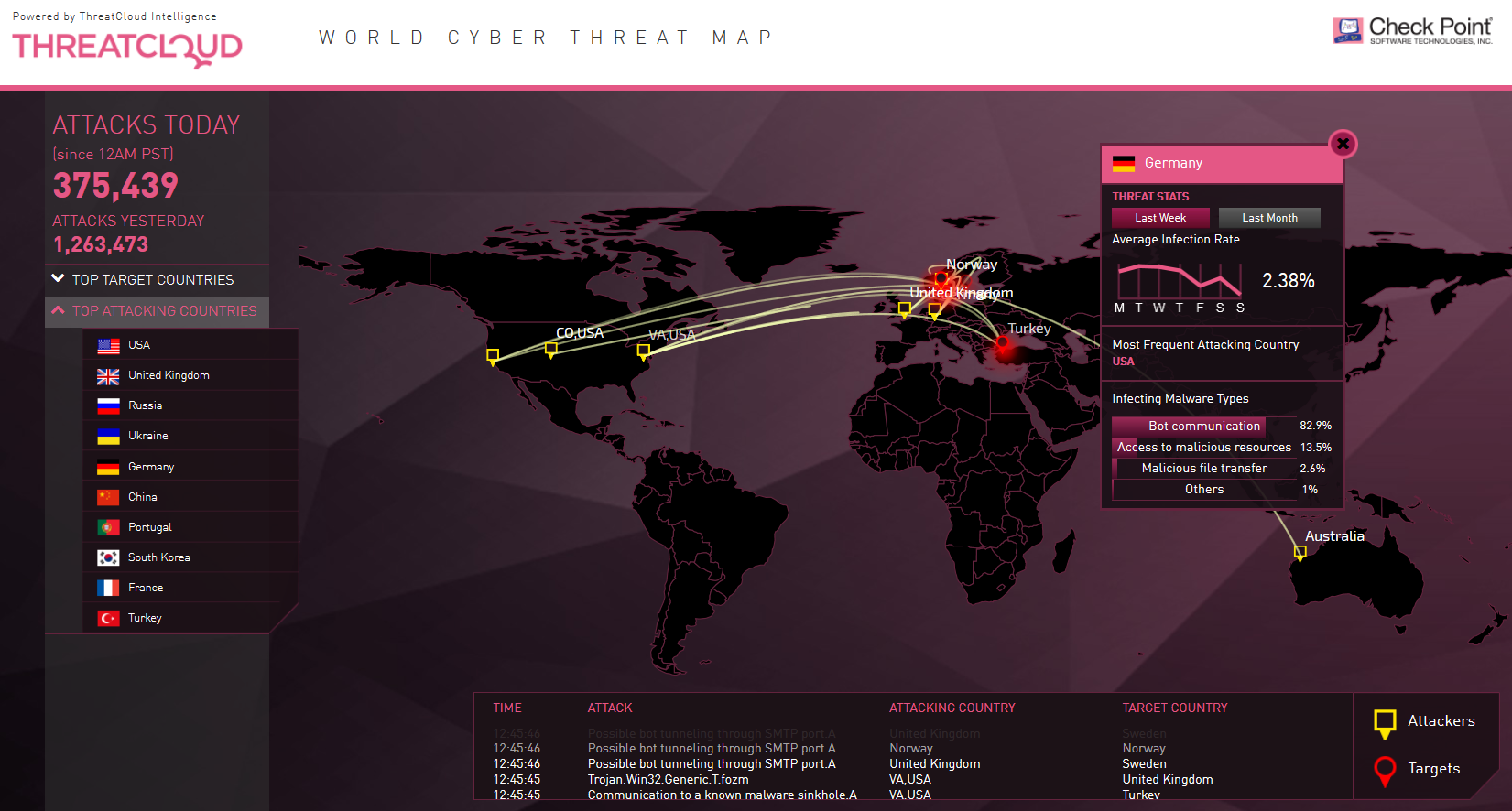
It’s interesting to watch who is initiating cyber-attack whom globally live. Thousands of website gets hacked every day due to vulnerable files, plugins, misconfiguration on the servers. Check Point Software Technologies Inc. If your website owner or administrator, you can perform security scan against your website to check vulnerabilities and malware. A cyber attack is a strike against a computer system, network, or internet-enabled application or device.
Victims of cyber attacks can be random or targete depending on cyber criminals. Digital Attack Map - DDoS attacks around the globe. Copy this code into your dismiss. Shows both large and unusual attacks.
Attack Bandwidth (), Gbps Dates are shown in GMT Data shown represents the top ~ of reported attacks. Increased productivity using SmartConsole Extensions. The ThreatCloud database holds over 2million addresses analyzed for bot discovery, over million malware signatures and over 5. More and more security companies use a webpage to show their monitored global security events such as the Live Status of Cyber Attacks being launched from where and who is the target of that attack. It is become interesting by watching those websites.
Actually those are not games but actually happening globally. Kaspersky CYBERTHREAT REAL-TIME MAP 2. Latest check days ago. With some maps, you can watch a live feed of attacks happening worldwide. FireEye Cyber Threat Map. Real-Time Cyber Attack Threat Map.
It is your one-stop global search and filtering tool to quickly locate relevant technical documentation, SecurityKnowladge solutions, software downloads, tools, and product forum topics. Wenn du die Website weiterhin nutzt, stimmst du der Verwendung von Cookies zu. At the bottom, you can see the source, type of attack , and target with the time of the attack. We are talking about the impressive Live Cyber Attack Threat Map , that as its name says, is a map that shows all the cyber attacks that are ocurring in the world in real time. A cyber threat map , also known as a cyber attack map , is a real-time map of the computer security attacks that are going on at any given time.
In this talk we will take you on a journey through the current trends in the cyber threat landscape and show how they may. Although the cyber - attack which disrupted the IT infrastructure of the. Dynamic Threat Defense - LookingGlass Dynamic Threat Defense (DTD) is a LookingGlass cyber security solution that utilizes the Cyveillance Malicious CData Feed to automatically mitigate threats via LookingGlass DNS Defender. DTD allows your organization to be automatically protected from threats such as embedded malware, viruses and trojans.
In addition to watching the playback, the top attackers and targets can be viewed historically, with monthly and weekly stats. But what is the Norse Attack Map exactly and what does it all mean? It certainly looks cool, but is it accurate?
Take a look at a live threat map to see where cyber attacks are originating and landing. Home CXO FILES Seeing is believing: live threats in action. Norse’s live cyber attack map may be the most comprehensive one available to the public. The company claims to have the largest dedicated threat intelligence network in the world.
It collects data from more than million “sensors” — honey pots that convince hackers that they have broken into the targeted system when actually they have. The Norse Attack Map is a powerful way to demonstrate to people that the threat of Cyber -attacks is real. The LookingGlass portfolio is purposefully-designed to address digital risk at every stage of the cyber attack cycle. Our outside-in view of threat helps organizations determine the risks that matter most to them – not just what’s trending in the news. View global threat activity — infections, live attacks and botnets.
At the same time, the report says banking malware is currently the biggest threat to mobiles. A full report going forward. Which are offering the industries most advanced threat prevention against 5th generation cyber -attacks. These modular gateways come in base, plus, and turbo models depending on the throughput and performance required for your application. The attack simulations are conducted on virtual models that are automatically generated and will not interact with the actual environment in any way.
CAD Vanguard leverages the vast amount of data available in AWS to automate threat modeling of cloud environments and bring unprecedented insight with cutting edge attack simulations.
Hiç yorum yok:
Yorum Gönder
Not: Yalnızca bu blogun üyesi yorum gönderebilir.