Shows the top reported attacks by size for a given day. Shows attacks on countries experiencing unusually high attack traffic for a given day. A Distributed Denial of Service ( DDoS ) attack is an attempt. Kaspersky Cyber Malware and DDoS Real-Time Map. Once you load the map, it detects your current location and show you stats for your country, including historical top local infections for the last week.

See recent global cyber attacks on the FireEye Cyber Threat Map. Dynamic Threat Defense - LookingGlass Dynamic Threat Defense (DTD) is a LookingGlass cyber security solution that utilizes the Cyveillance Malicious CData Feed to automatically mitigate threats via LookingGlass DNS Defender. DTD allows your organization to be automatically protected from threats such as embedded malware, viruses and trojans. Top daily DDoS attacks worldwide. A massive attack targeted KrebsOnSecurity, a leading cyber-security researcher.
Attacks on Brazil during and shortly after the Rio Olympics. Norse Map Ddos Atanların Evlerini Buluyoruz - Duration: 5:01. Attacks are visualized as an arc that travels from the source of the attack to its target.
This isn’t a real-time cyber attack map, but that doesn’t make it any less. New DDoS Threat Intelligence Map from A10. A10’s DDoS map give you insights into where the next DDoS attacks will come from. By combining this knowledge with A10’s actionable DDoS threat intelligence platform, Thunder TPS, you can. When it comes to real-time cyber attack maps, some are funny, some seem ominous, and all of them tell a story that words alone cannot: cyber attacks never stop.
Interactive cyber -attack map by HTTPCS : Real time Website attacks, Vulnerable Websites, Malicious Websites, Malware providers. Search a specific domain or a word. Take advantage of our free discovery offer to be alerted of cyber attacks and public security flaws related to your domain name. Ever want to see a visual map of cyber-attacks?
Sure you do… We talk a little bit about security, keeping safe online and how to keep your data secure in the case of a threat. One of the major threats to websites and data centers is DDoS attacks: Distributed Denial of Service. They all seem to show the cyber attacks in a slightly different perspective.
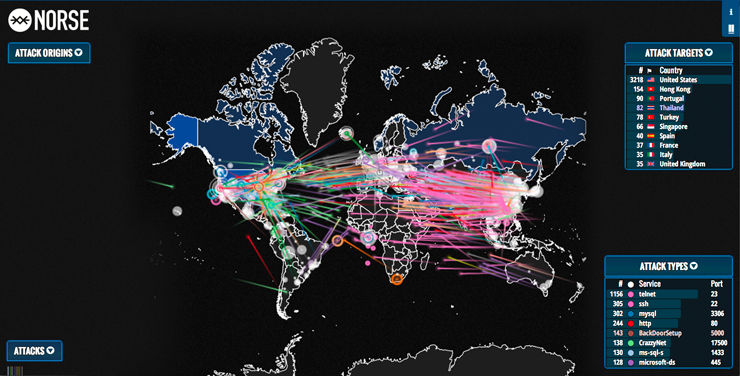
This is the Norse attack map as an example: Here is a brief overview of each map : 1. Home Cyberwar The best Live Cyber Attack maps. They claim the following about their cybercrime map : This map of Britain shows cyber crime records amongst police forces, following FOI requests from TechWeekEurope. What is the Norse Attack Map ? The Norse Attack Map is basically an interactive map , created by Norse Corporation, which shows, in real-time, global cyber attacks, in the form of colourful laser beams which zip across your screen. About Threatbutt Internet Hacking Attack Attribution Map By leveraging our patented Clown Strike technology we are able to harness the raw power of private, hybri public and cumulus cloud system to bring Viking grade threat intelligence to any enterprise. And we made it into a map.
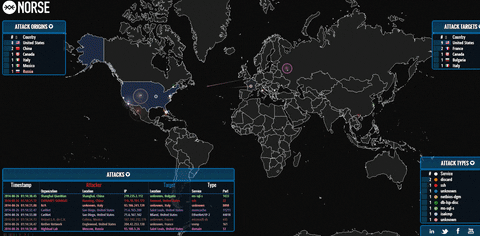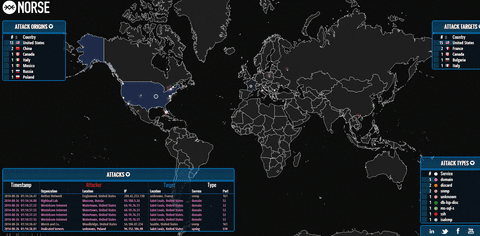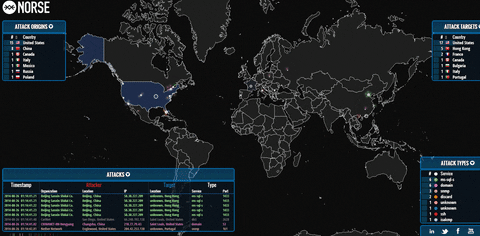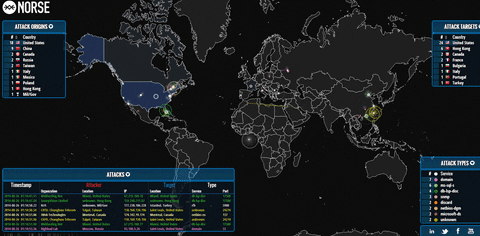
Powered by pewpew, even though we made it more accurate because we are a company that does the best threat stuff. ANetworks has created the DDoS Threat Intelligence Map. Bringing down a service is achieved by spamming it heavily with traffic from different places by tapping into various computers and requesting them to access the target. The DDoS attack map shows all the current attacks happening in real time all over the world.
DDoS attacks are a calculated effort to hit an online service where it matters: uptime. It is also a good practice to install the monitoring and notification system recognizing the attributes of a DDoS attack, which will help react to a threat in time and take necessary actions. Real-time global botnet threat map. View the IP address locations of servers used to control computers infected with malware. now for a free 30-day trial.
If you haven’t seen these maps, it can be eye opening. One of the easiest ways to silence someone online is a distributed denial of service attack (DDoS). But it’s difficult to solve a problem you can’t see.
Hiç yorum yok:
Yorum Gönder
Not: Yalnızca bu blogun üyesi yorum gönderebilir.